What?
Previously, non-administrators could install signed and unsigned drivers, but CVE-2021-34527 documented a critical vulnerability in the Windows print spooler allowing remote code execution. AKA “PrintNightMare” (a metaphorical nightmare for sysadmins all over)…
At this point, you should have the print spooler service disabled on all non-print servers to secure your environment.
If your print manufacturer offers V4 drivers, you’ll want to install those and get rid of the V3 drivers. However, not all manufacturer print drivers support functions like Auth Tracking (looking at you Konica Minolta).
Resolution Paths:
The first option, if you are hybrid Azure Active Directory or Azure Active Directory, should be to utilize the Microsoft Universal Print connector and deploy printer shares through Azure. However, this does have MS licensing requirements.
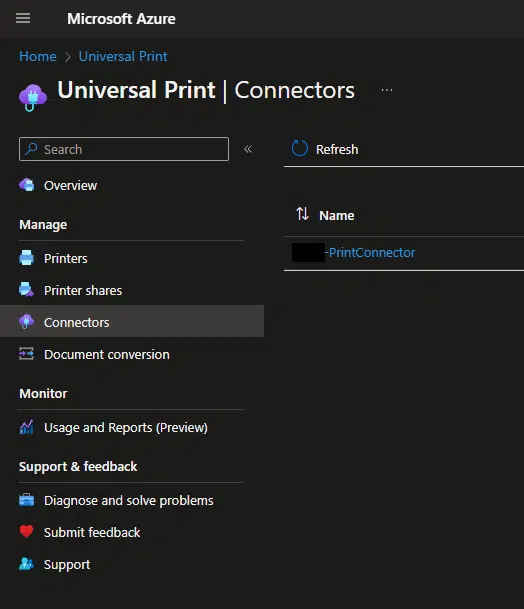
To do this, you need to:
- Install the Universal Print Connector App on your printer server(s).
- Sign in with an organizational admin or another Azure account with privileges to manage the application.
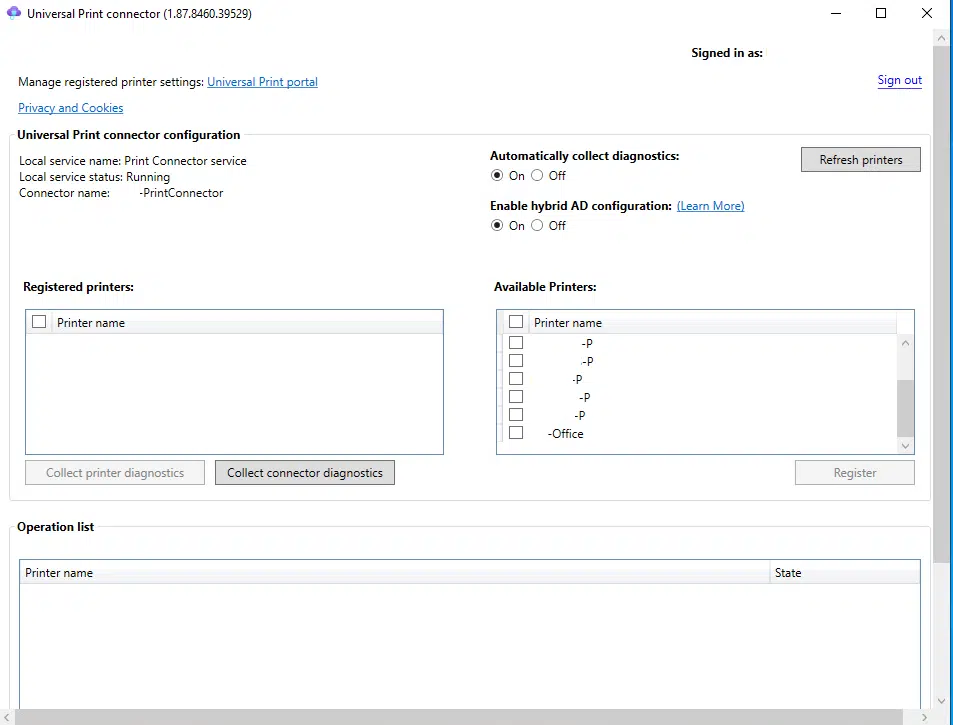
- From the connector app, you will now see the list of available printers on your server.
- You can add desired printers to be registered with Azure for a modern print deployment solution.
- Registered printers will show in Universal Print within the Printers blade.
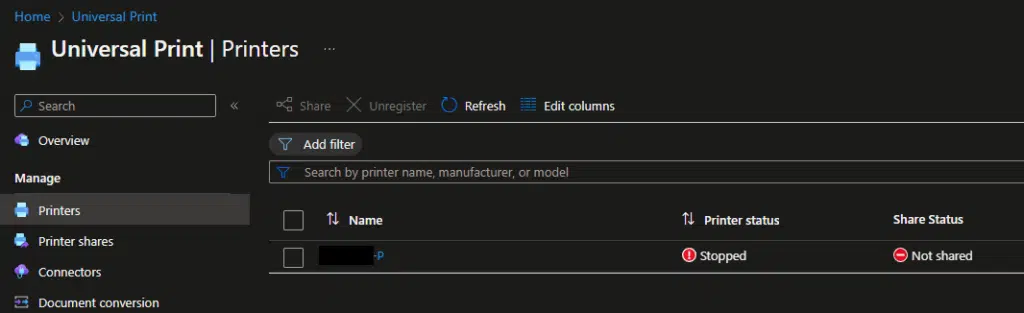
- Finally, in the Printer shares blade, you can add a share for the desired printers and user groups. As long as the user’s endpoint has the Intune Management Extension on their device, your end users will be able to print to the local printers available to them.
The next option, for hybrid AD and local-only AD environments, is to publish a two-part restriction to allow users to install the drivers, but only from your designated print server(s).
Note: the registry changes can be published through Intune as well, but it may be more beneficial to use Universal Print or a third party solution.
- Publish a registry change to your target computers (can create a script to be deployed with Group Policy Management Console) allowing workstation users to install drivers without admin credentials.
- CMD
reg add "HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows NT\Printers\PointAndPrint" /v RestrictDriverInstallationToAdministrators /t REG_DWORD /d 0 /f
PowerShell
Set-ItemProperty -Path Registry::"HKLM\SOFTWARE\Policies\Microsoft\Windows NT\Printers\PointAndPrint" -Name "RestrictDriverInstallationToAdministrators" -PropertyType "DWORD" -Value "0" -Force
- Next, publish a GPO to your target user/workstation OU(s) to restrict package point and print servers (and depending on your environment, you may need to restrict driver installs entirely using the Point and Print Restrictions policy).
- List your print server in the approved server list.
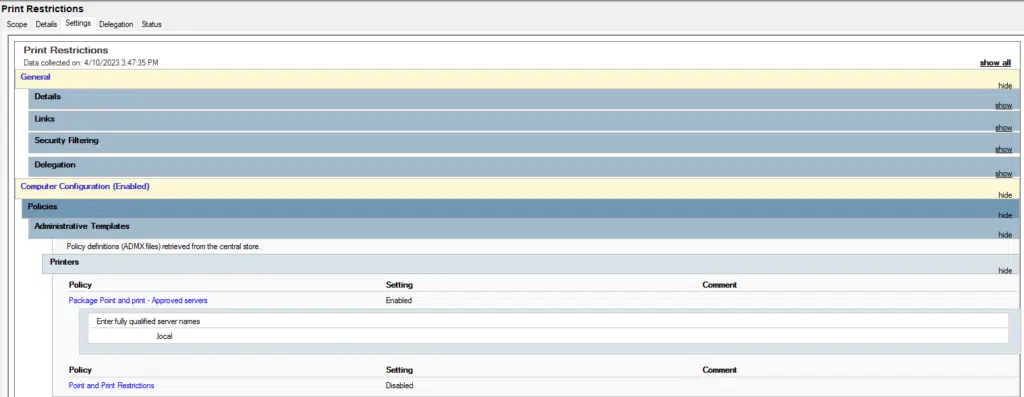
- Now, you can deploy your printers to your OUs as you always have and end users will again have their printers available to them.
The last option is to implement a third-party cloud print solution, like PaperCut or PrinterLogic.
Resources:
- https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-34527
- KB5005652—Manage new Point and Print default driver installation behavior (CVE-2021-34481) – Microsoft Support
- License Universal Print | Microsoft Learn
- Free Google Cloud Print alternative – Mobility Print | PaperCut | PaperCut
- Eliminate Print Servers | PrinterLogic