I’d like to start with, we are big advocates for 3CX and it’s a very solid VoIP service. You can’t go wrong with over 500k customers and millions of users.
What Happened?
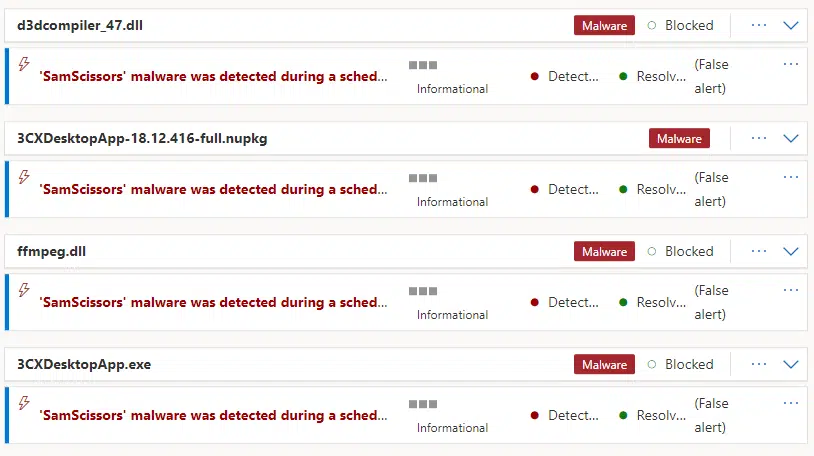
3CX suffered a supply chain breach where a cyber threat actor (possibly Labrynth Chollima) compromised the desktop application and was able to manipulate the ffmpeg.dll file to sideload crypto stealing malware. An internal breach compared to the likes of Kaseya and SolarWinds. Sentinel One began flagging the software nearly a week before it became known to be compromised and most SOC analysts were labeling it as false. On Wednesday, March 29th, a very thorough report by CrowdStrike found the desktop application to be communicating with multiple domains that were not affiliated with 3CX. These indicators of compromise were investigated. It was further revealed that the signed .msi file, once installed, placed 3 additional files through the compromised ffmpeg.dll. Enough evidence exists to assume the threat actors had access to 3CX systems for months before the exposé.
IoC domains:
- akamaicontainer.com
- akamaitechcloudservices.com
- azuredeploystore.com
- azureonlinecloud.com
- azureonlinestorage.com
- dunamistrd.com
- glcloudservice.com
- journalide.org
- msedgepackageinfo.com
- msstorageazure.com
- msstorageboxes.com
- officeaddons.com
- officestoragebox.com
- pbxcloudeservices.com
- pbxphonenetwork.com
- pbxsources.com
- qwepoi123098.com
- sbmsa.wiki
- sourceslabs.com
- visualstudiofactory.com
- zacharryblogs.com
What is the appropriate response?
- Ensure your EDR/AV is updated on your endpoints.
- Remove any instances of devices with the 3CX desktop app acquired to the .msi installer. You may need to do more than that if your end users had admin privileges to their endpoints and/or you have a typical AD domain.
- Switch to using the PWA (Progressive Web App) and/or standard desk phones. The PWA functions exactly the same without the compromise.
- Continue watching network logs for the indicators of compromise.
- Update your firewall inbound and outbound policies. You should by default secure both ingress and egress.
- Find a qualified service provider like RackSimply to help you mitigate this breach and provide you with an EDR or MDR solution to stay in front things like this.
The Summary
It’s never a question of if but a matter of when. There will always be breaches and the best you can do is practice a least-privilege model, strict identity management, and strict data management and retention.
Check your vendor contracts and ensure that service providers (SaaS, IaaS, NaaS, PaaS, etc) are stepping up to the plate to secure your data AND theirs. A breach will always come through the weakest link.
Resources:
- https://www.reddit.com/r/crowdstrike/comments/125r3uu/20230329_situational_awareness_crowdstrike/
- https://learn.microsoft.com/en-us/microsoft-edge/progressive-web-apps-chromium/how-to/
- https://sansorg.egnyte.com/dl/fyF6fGJ4lz
- https://www.sans.org/media/score/checklists/FirewallChecklist.pdf
- https://en.wikipedia.org/wiki/Kaseya_VSA_ransomware_attack
- https://en.wikipedia.org/wiki/2020_United_States_federal_government_data_breach
- https://learn.microsoft.com/en-us/windows-server/identity/ad-ds/plan/security-best-practices/implementing-least-privilege-administrative-models
- https://www.microsoft.com/en-us/security/business/security-101/what-is-identity-access-management-iam
- https://learn.microsoft.com/en-us/azure/security/fundamentals/data-encryption-best-practices