HPE
What to do about recently announced certificates expiring for Palo Alto Firewalls
December 16, 04:30
0
There is quite a ruckus with the community because of Palo Alto expiring certificates on all Firewalls. The expiring certificates affect dynamically updated services like Wildfire, GlobalProtect HIP, URL filtering, DNS Security, Threat Vault, Etc. Essentially, the firewall will lose trust with Palo Alto updates services.
Original advisory (login required) PAN-OS Root and Default Certificate Expiration
If you are not using Ansible for automated configuration management and would like to, Palo Alto has a collection available among others : Palo Alto Networks GitHub
A few actions must be taken for your PA NGFW:
Scenario 1: Customers with Data redistribution and private cloud appliances must upgrade their firewalls or deploy custom certificates.
If upgrading, a targeted version as specified in the table below is required.
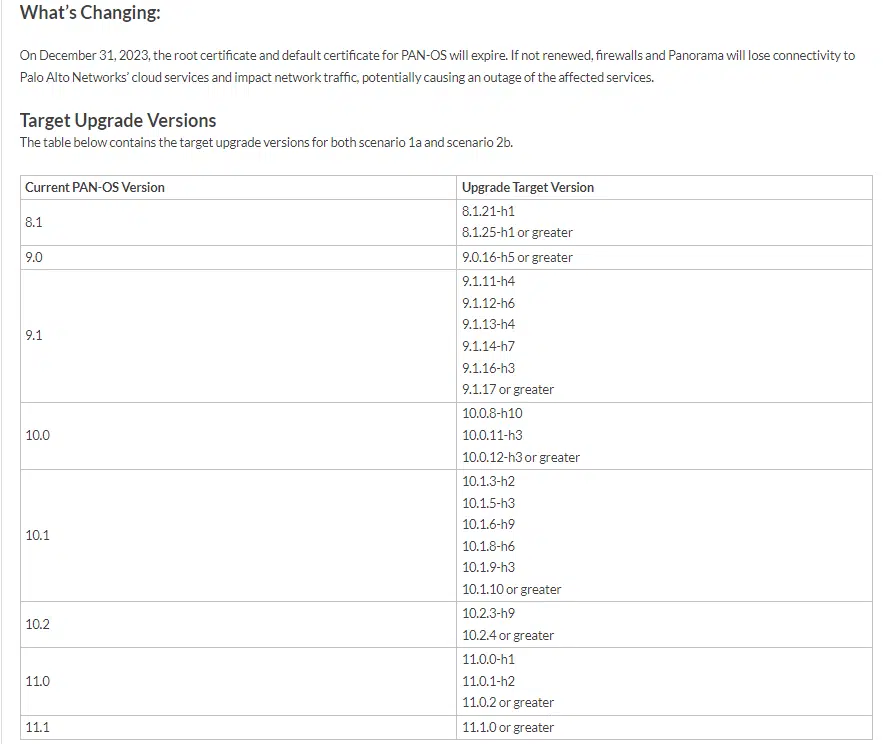
If an upgrade is not desired or practical, deploying custom certificates and switching the data redistribution agent and client over is necessary. Setup Custom Certificates and Configure data redistribution
Scenario 2:
Customer is using URL filtering, DNS security, Wildfire public cloud, Threat vault.
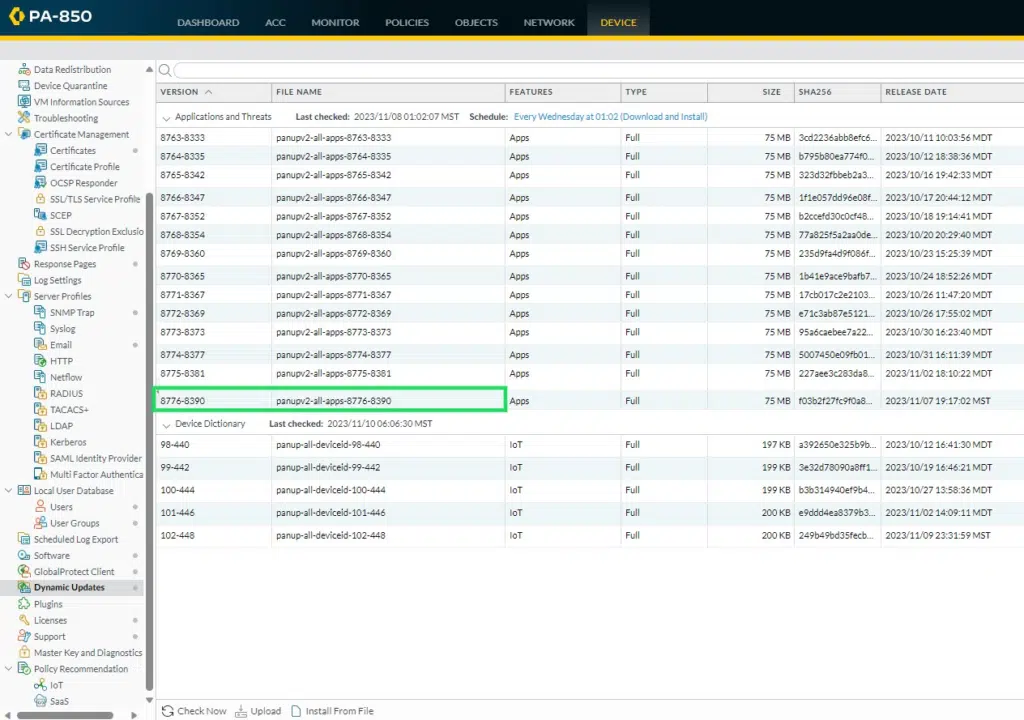
Install specific content update version 8776-8390 or later on firewalls (if updates are not automatic).
Or
Upgrade firewall to one of the aforementioned verions.
Or
Enable device certificate (though is not recommended on older versions 8.1, 9, and 9.1) Device Certificate
Show Your Support
LinkedIn
Facebook
Twitter